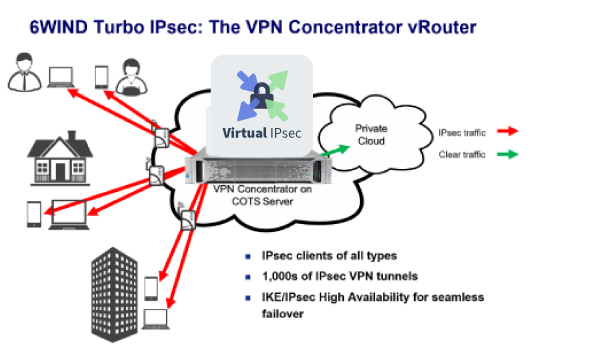
VPN Concentrators are networking devices in router form factors that provide secure VPN connections and delivery of traffic between VPN nodes. Whether it is the usage of cloud providers such as AWS, Azure or Google, the expansion of local decentralized offices, employees working from remote locations or the Internet of Things (IoT), more internal data flows are crossing untrusted communication networks. In response, Service Providers deploy VPN Concentrators specifically to create and manage secure VPN infrastructure to provide services for customers.
Thanks to innovations in networking software based on Intel architecture, Service Providers can now deploy VPN Concentrator functionality in Virtual Border Router (vRouter) solutions, on white box servers, and inside virtual machines as an alternative to expensive hardware. In today’s blog I will review our VPN Concentrator vRouter features, performance, management and monitoring and conclude with an overview of our current demo.
6WIND Virtual Security Gateway, Based on Intel architecture, Gives Service Providers a Software Alternative
6WIND’s VPN Concentrator vRouter is deployed through 6WIND’s Virtual Security Gateway software network appliance. 6WIND Virtual Security Gateway is the industry’s high-performance software alternative, giving Service Providers the features and power to run VPN Concentrator solutions on Intel-based servers in vRouters instead of hardware routers. Features include IPsec VPNs, protection mechanisms against DDoS attacks, VRRP and IKE/IPsec High Availability for seamless failover and advanced monitoring through Key Performance Indicators exported to an analytics dashboard.
6WIND Virtual Security Gateway vRouter Performance
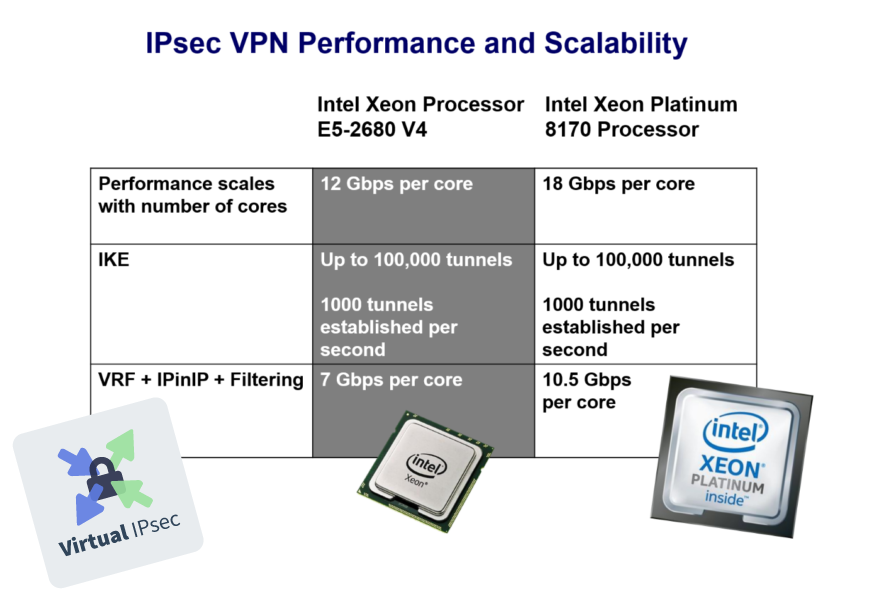
6WIND’s benchmarks, built on dual Intel Xeon Platinum 8170 processors, shows increased performance by 50% versus the previous generation. We can deliver 18 Gbps per core and 10.5 Gbps per secure VPN tunnels. 6WIND software scales linearly with the number of cores. If you need more performance, simply add more cores to the configuration. Without any change in the vRouter software, the IPsec performance is greatly improved by just updating the server to the latest hardware. The 2nd generation Intel Xeon Platinum processors benefit from additional performance increases with 6WIND vRouter as well. See my previous blog on this topic.
NETCONF/YANG for Open Management
6WIND Virtual Security Gateway’s vRouter’s management is based on NETCONF and YANG. The CLI itself is a NETCONF client that comes with traditional features such as completion, history and contextual help. It relies on a YANG data model that users browse as they would browse a file system. Relative and absolute paths can be used to refer to configuration data, making browsing very efficient. This allows for integration with third-party management frameworks and offers APIs for an automated, programmatic configuration of the vRouter. The CLI includes configuration commit with rollback on error and simultaneous access with configuration comparison.
YANG-based KPIs for Telemetry
In addition to granular monitoring, YANG-based Key Performance Indicators (KPIs) are provided for streaming to a time-series database. The vRouter tracks statistics against time and therefore has a thorough understanding of the system dynamics to better optimize the configuration. The time-series information can be displayed in a graphical analytics framework such as InfluxDB/Grafana. The same APIs can be used for integration with other frameworks, such as Elastic Stack, Prometheus and more.
High Performance VPN Concentrator vRouter Based on Intel Technology
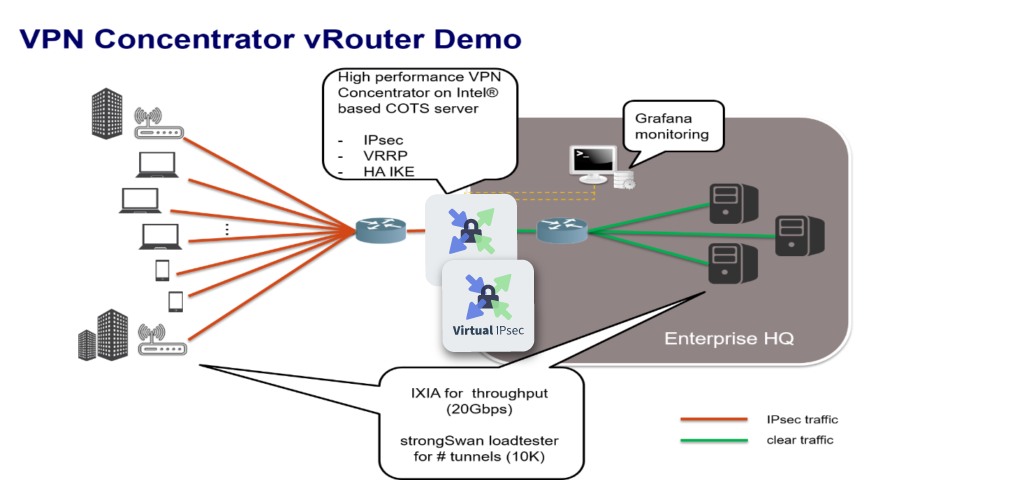
This is our demo platform, with the VPN Concentrator sitting at the edge of the enterprise headquarters. Remote workers and enterprise subsidiary sites open IPsec tunnels towards the VPN concentrator for a secure connection to the enterprise resources.
The VPN concentrator is composed of two 6WIND Virtual Security Gateway instances working in High Availability mode, with VRRP for redundancy and IKE HA for seamless failover, thanks to the continuous synchronization of IPsec security policies and associations. The cluster is monitored using the Grafana visualization tool.
We run each vRouter instance on 5 cores / 10 threads of a dual-socket platform equipped with Intel Xeon Platinum 8170 CPUs running at 2.10 GHz. Each instance is allocated 8GB of RAM. We use an IXIA XM2 traffic generator to inject traffic at high rate and we emulate up to 10K remote IPsec connections thanks to strongSwan’s loadtester tool running on a separate platform.
This shows how 6WIND’s vRouter can be deployed on a standard off-the-shelf server as a VPN Concentrator to terminate 10K IPsec tunnels, maximizing throughput on a 10 Gbps link and providing redundancy and seamless failover, with all of this being monitored in a graphical environment. In our demo, we used 5 cores per VPN concentrator instance and 8GB of RAM, knowing that throughput scales with the number of cores and number of tunnels scales with memory.
This demo shows the power and flexibility of our VPN Concentrator vRouter as an alternative to hardware. In summary:
- Features: VRRP provides a single IPsec endpoint in both directions and IKE High Availability is configured for seamless failovers
- Performance: 10,000 tunnels sustaining 10 Gbps in both directions
- Management: NETCONF/YANG management engine allows monitoring of VPN Concentrators with secure traffic
- Monitoring: YANG-based KPIs integrated with the InfluxDB Time-Series Database and the Grafana analytics dashboard
Our evaluation program is now open for users who would like to test drive a VPN Concentrator vRouter on Intel architecture.
We look forward to hearing from you.
Jean-Mickaël Guérin is 6WIND’s CTO
Intel, the Intel logo and Xeon are trademarks of Intel Corporation in the U.S. and/or other countries.