On the other hand, in operational networks the conditions are different as everything is dynamic: ARP/NDP entries appear and disappear, IP routing tables are updated by BGP or OSPF routing protocols, IPsec Security Associations are negotiated through IKE, etc.
All these dynamic elements are used by the data plane. If an ARP is missing, a new ARP resolution will be required, otherwise, missing route packets will be dropped and missing IPsec SAs will trigger IKE negotiations. All these operations will lead to packet loss, which reduces data plane performance.
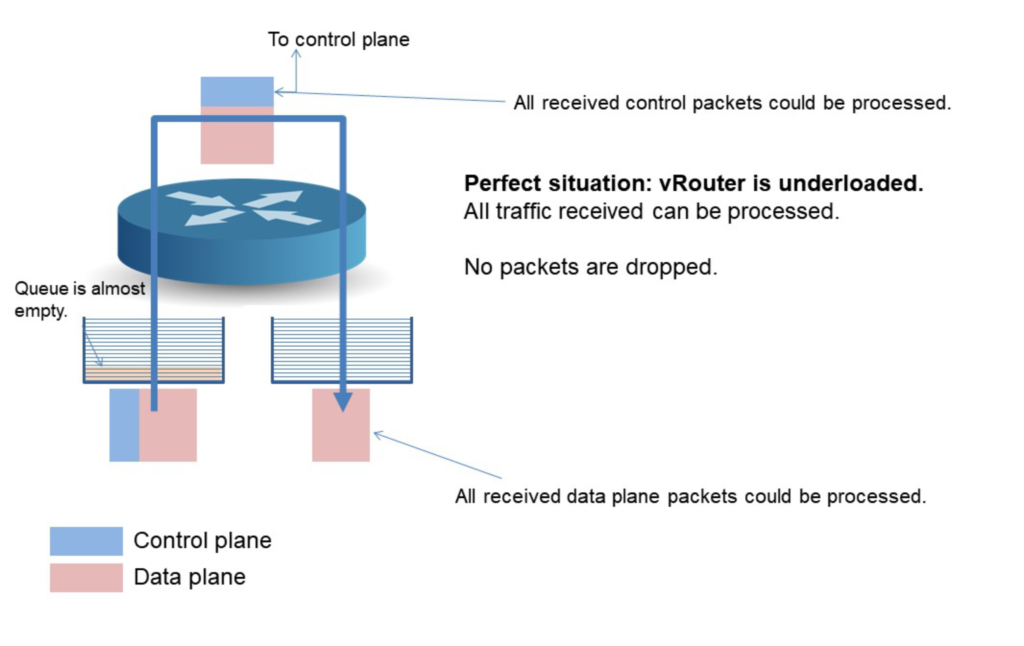
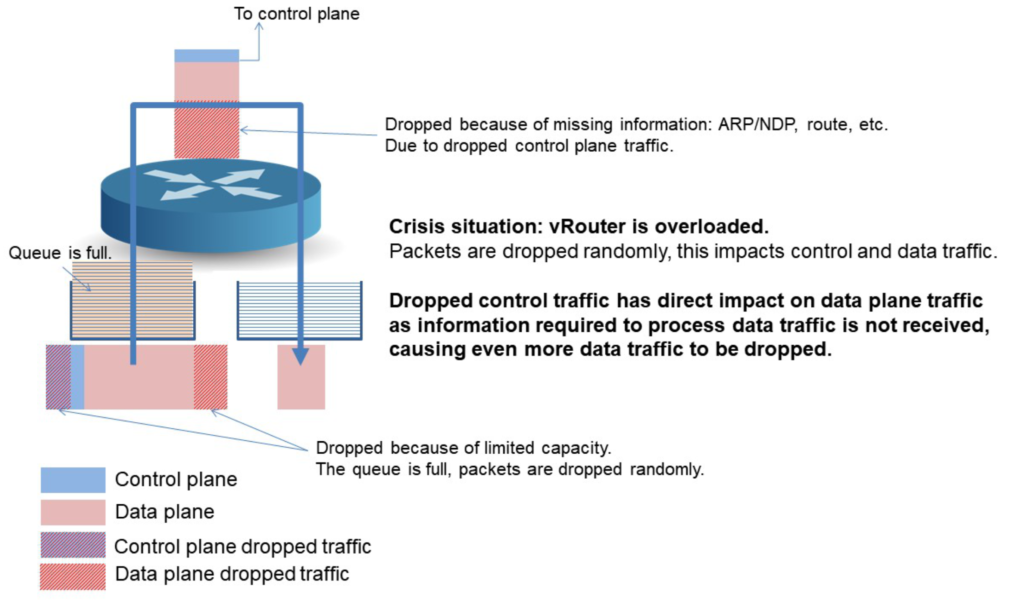
In a perfect world, the control plane traffic would be totally isolated from data plane traffic. However, we have to deal with reality; they are sharing the same pipes. And when the pipe gets full, random packet loss will happen, no matter if this packet is important or not. By important I mean if a unique packet loss will imply thousands of packets to be lost as well or if the loss will be limited to this unique packet.
Based on this definition, control plane packets are more important than data plane packets.
QoS’s objective is to prioritize and queue traffic. But in this case, these techniques are not efficient enough as they happen too late in the packet processing process (packets may already be lost at the NIC level), and its associated cost in CPU processing will make things even worse (more packets will be lost).
An effective way to protect the control plane traffic must be implemented according to these principles:
- Packet identification must happen as soon as possible
- Lightweight processing should only distinguish important packets based on their protocol and have two options: keep or drop
- Dynamic processing should be enabled only when it is required
6WIND’s vRouter solutions implement this control plane protection by monitoring the queue filling and allocating a CPU budget for this protection.
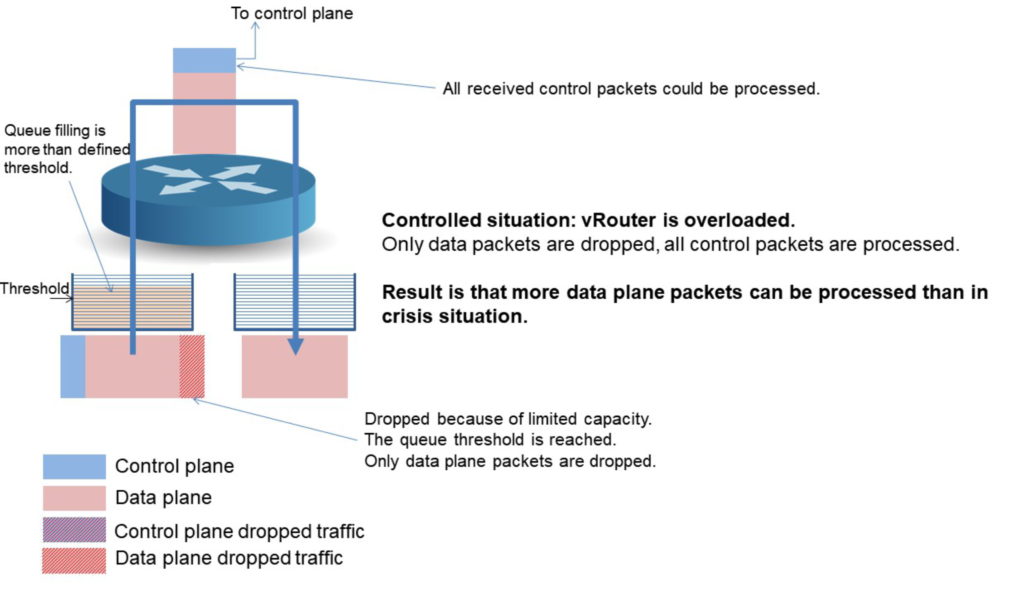
As soon as a queue is reaching its threshold, packets are dropped according to packet type. Control packets are preserved while data packets are dropped to reduce the queue filling under the defined threshold.
This keeps ARP, NDP, VRRP, IKE, BGP, OSPF, LACP and others unaffected by a system overload.
Let’s consider a scenario.
It all starts with an under-loaded vRouter: all packets received can be processed, the sky is blue, the grass is green, and everything is in perfect harmony.
Then everything goes wrong. It is Super Bowl Sunday, there is a brand new iOS release, a new Windows Service Pack, a new Game of Thrones (GOT) season available and international hackers decide it is the right moment to launch a new attack. Let’s call it: “Internet Doomsday.”
All packets are out for themselves struggling to find a way within the Rx queue to meet an accommodating CPU to be processed. There’s no luck for those arriving too late.
Control plane packets are dropped, which will lead to reduced data plane traffic or even worse to an inoperative router leaving your users with no Bowl, no GOT and nothing but sorrow and despair.
But if you were wise enough to get a vRouter from 6WIND, the situation would be better. Control packets would be preserved by dropping data packets. This will reduce the overall bandwidth processed, but the system will stay up for all users.
By sacrificing a few identified packets early, 6WIND’s vRouter maximizes the number of packets to be properly processed. This is a sound investment.
Contact 6WIND today to evaluate our vRouter solutions with control plane protection.