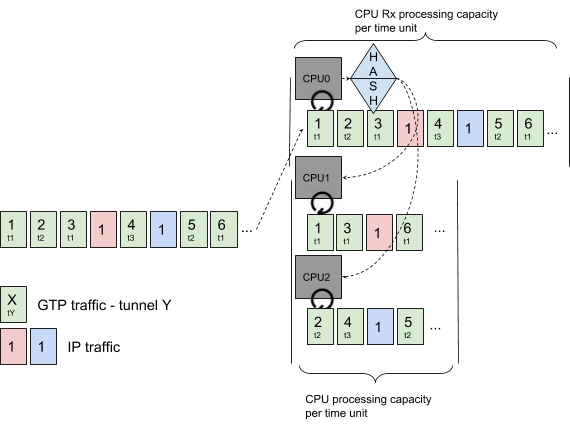
The approach described used one CPU to receive the packets and dispatch them, according to a specific key, to other CPUs for further processing.
This enables good performance and guarantees packet ordering.
This works well when the key varies and produces different hashes. For example, the GTP teid can be used to distinguish the multiple GTP tunnels and dispatch them on different cores.
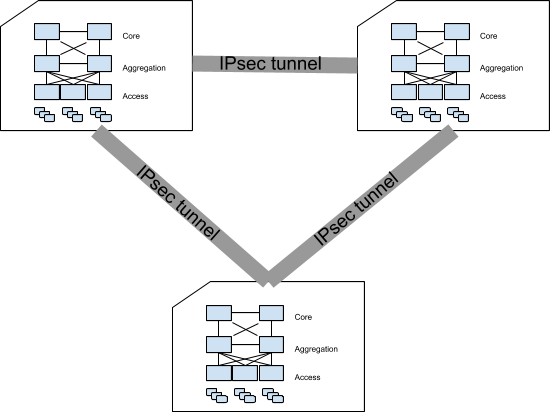
Now, let’s consider the interconnection of data centers, when the traffic is protected through IPsec tunnels.
Data centers are connected in full mesh: one IPsec tunnel is set up between each pair of data centers.
As soon as the traffic becomes important, having a single IPsec tunnel becomes the bottleneck for efficient communication between data centers.
Problem Statement
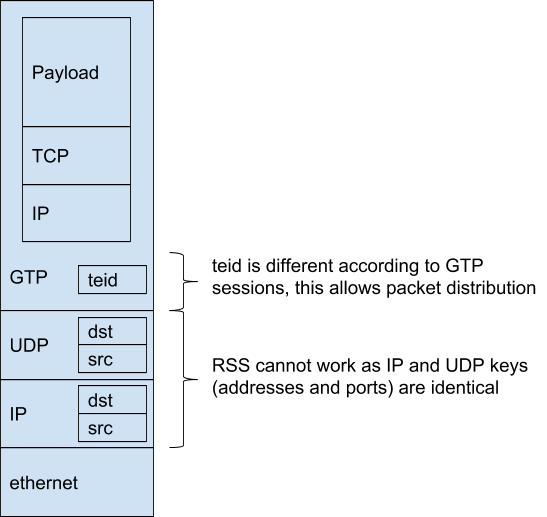
Single IPsec tunnel traffic cannot be load balanced easily as the encapsulating header doesn’t vary and the contents of the payload cannot be accessed.
In the header, IP addresses are always the same and the IPsec SPI is unique as well. The payload content is protected by IPsec, meaning you cannot use it to dispatch packets.
Typical performance achieved by 6WIND Virtual Security Gateway vRouter is about 12 Gbps of IPsec traffic with 1500 byte packets on a single CPU. As IPsec traffic cannot be processed through RSS or load balancer this would limit the overall communication between datacenters to 12 Gbps.
At 6WIND we believe 12 Gbps is not enough, as do our customers, so as a consequence we figured out a way to support more traffic within a single IPsec tunnel.
6WIND Offers vRouter IPsec Solutions
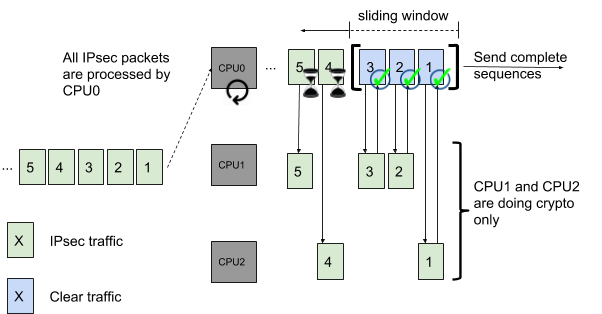
6WIND’s Virtual Security Gateway vRouter solution is to have one CPU offload the crypto operations to other CPUs according to their load, while preserving packet ordering per flow. The receiving CPU is in charge of checking the crypto operation completion before clear packets are sent for further processing.
In this example CPU0 receives all packets as there is only one IPsec tunnel. It offloads crypto operations to CPU1 and CPU2 according to their load.
Once a complete ordered sequence has been processed, packets 1, 2, 3 are sent for further processing. This keeps packet ordering according to IPsec packets received.
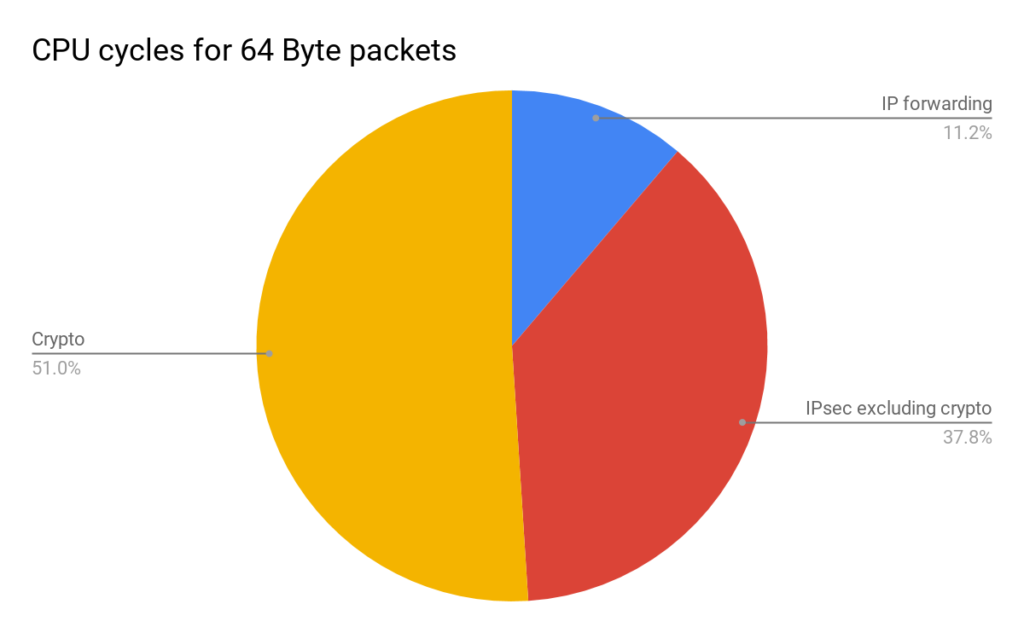
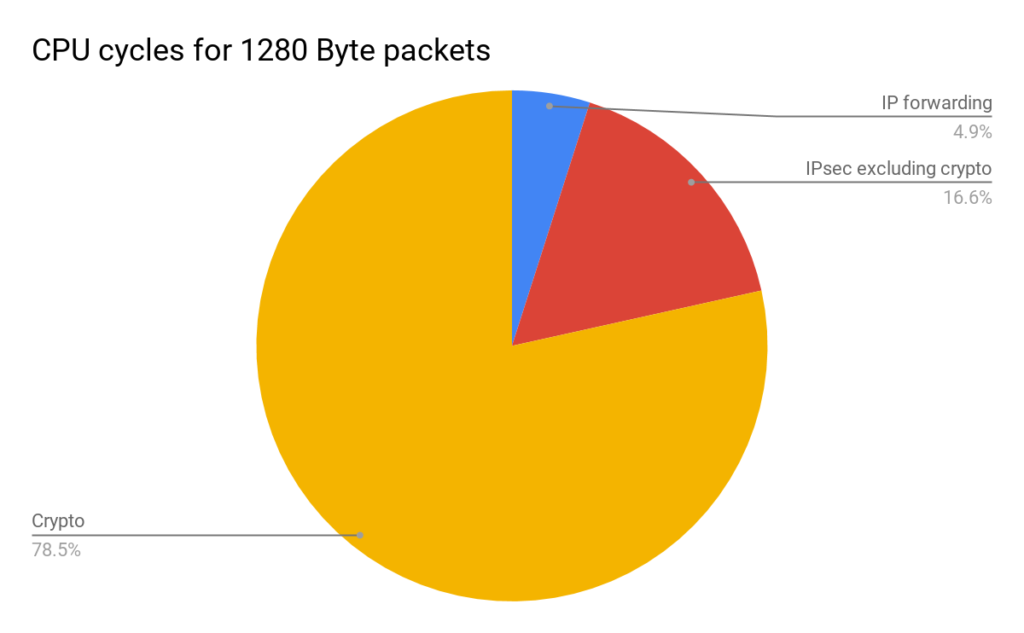
This solution offloads the costliest part of IPsec processing. 64B packet crypto operations represents roughly 50% of cycles used for packet processing. 1280B packet crypto represents 78% of the cycles.
In this case offloading crypto operations can double the overall IPsec system performance.
In this case the performance can be multiplied by 4 offloading crypto operations.
Conclusion
As a conclusion 6WIND Virtual Security Gateway vRouter creates high performance for single IPsec tunnels by offloading crypto operations. Packet ordering is preserved and no traffic engineering is required.
Contact us today to discuss the performance requirements for your vRouter deployment scenarios. We are happy to share our expertise.
___________________________________________________